Think of it this way: when you buy a ticket to a movie, you’re buying the right to watch that film one time, in that specific theater. You can’t legally record it, and that ticket stub won’t get you into another showing tomorrow. DRM-protected content applies that same idea to the digital world.
It’s essentially any digital media—a movie, a song, an ebook, or software—that has a technological “lock” on it to control how it’s used. This system, known as Digital Rights Management, is what prevents things like unauthorized copying, sharing, or playback, making sure that creators and distributors stay in control of their work.
What Is DRM Protected Content in Simple Terms

At its heart, Digital Rights Management is a set of access control technologies. Publishers, copyright holders, and individual creators use it to apply a specific set of rules to their digital media.
This is the system that makes sure when you stream a new series on Netflix or listen to a playlist on Spotify, you’re doing it according to the terms of your subscription. It’s the invisible guardrail of digital content.
The Role of a Digital Lock
It helps to think of DRM as a really sophisticated digital lock. Only a user with the right “key” can open that lock and access the content. So, what’s the key?
The key is a secure license that your device—whether it’s your phone, laptop, or smart TV—requests from a license server the moment you hit play. If the server confirms your account is active and your device is authorized, it hands over the license. The content then plays instantly.
This whole back-and-forth happens in milliseconds, completely behind the scenes, so you don’t even notice it. The goal is a seamless user experience that still respects and enforces the security rules set by the content owner. It’s this technology that enables the business models we use every day:
- Subscription Services: Getting all-you-can-eat access to a library of content for a monthly fee (think Hulu or Apple Music).
- Rentals: Paying a one-time fee for temporary access to a specific movie or show (like renting a film on Amazon Prime Video).
- Purchases: Buying ongoing access to a piece of content that you can watch on your authorized devices.
A Quick Summary of DRM
To really get a feel for what DRM protected means, it’s useful to see its core functions laid out. For a deeper dive into the topic, you can also explore our detailed guide that answers the question, “what does DRM mean” in today’s media landscape.
To start, let’s break down the fundamentals with a quick summary.
DRM Fundamentals at a Glance
This table offers a snapshot of the core concepts behind Digital Rights Management technology.
| Concept | Description |
|---|---|
| What It Is | A technological framework that applies specific rules and restrictions to digital content. |
| What It Does | Prevents unauthorized copying, distribution, and playback of copyrighted material. |
| Why It Matters | It protects revenue for creators and ensures that licensing agreements for premium media are enforced. |
In short, DRM is the essential technology that allows premium content to be distributed securely and profitably online.
How DRM Technology Protects Your Content
Knowing that DRM-protected content has a digital lock is one thing. Understanding how that lock actually works is another. It’s a carefully choreographed process designed to protect your media from the moment it’s created until the second a viewer hits play, all without getting in the way of their experience.
Think about it this way: you wouldn’t just upload your premium video to a server and hope for the best. That’s like leaving the door to a bank vault wide open. Instead, DRM wraps your content in several layers of security, creating a sealed-off workflow that vets every single request to watch it.
The First Step: Encryption
The journey starts with encryption. Before your video even gets close to an audience, it’s scrambled using powerful cryptographic algorithms. This essentially turns your perfectly watchable video file into unreadable nonsense, making it completely useless to anyone who doesn’t have the specific key to unlock it.
It’s a bit like shredding a highly sensitive document. Unless you have the precise instructions to piece it all back together, you just have a pile of confetti. This encrypted file is what actually lives on the servers and gets delivered to your viewers.
Creating and Securing the License Key
Of course, for every piece of scrambled content, there’s a decryption key that can make it whole again. This key is the digital version of those reassembly instructions—it’s the most critical piece of the security puzzle.
To keep this key safe, it’s never stored with the video file. Instead, it’s sent to a totally separate, highly secure server called a license server. This separation is the bedrock of DRM security. Even if a pirate somehow managed to grab the content file, they’d still be missing the one thing they need to make it playable. The license server is the gatekeeper, holding all the keys under its own lock and key.
The Core Principle of DRM Security: The strength of any DRM system comes from a simple but powerful idea: keep the encrypted content and the decryption key separate. This makes having one without the other completely useless, forcing every playback attempt through an official, authorized channel.
This division of labor makes unauthorized access incredibly difficult. A user’s video player has to prove it has permission to watch the content before the license server even thinks about handing over the key.
The Digital Handshake in Action
So, when a legitimate user wants to watch your video, their device kicks off a secure process often called a “digital handshake.” This all happens behind the scenes in a matter of milliseconds. It’s a quick but essential conversation between the video player, your streaming platform, and that all-important license server.
Here’s how that conversation usually goes:
- The Playback Request: A user clicks “play.” Their video player receives the encrypted content, but at this point, it’s just a jumble of data.
- The License Request: The player sees the content is protected and immediately sends a request to the license server. This isn’t just a simple “please”; it includes information to prove the user and device are legitimate.
- Authentication and Verification: The license server inspects the request. Is this a paying subscriber? Is their account in good standing? Are they trying to watch on a supported device?
- License Delivery: Once everything checks out, the license server sends the unique decryption key back to the player. This key is often temporary, good for just that one viewing session.
- Decryption and Playback: The player uses the key to unscramble the video content in real-time, right on the user’s device. The video starts playing, and the viewer is none the wiser about the complex security exchange that just happened.
This entire sequence makes sure that only authenticated viewers on authorized devices can ever decrypt and watch your content. It effectively shuts down common piracy tactics, because the video remains safely encrypted until the very last moment of playback.
Understanding The Major Drm Systems
The world of digital content isn’t a one-size-fits-all environment, and neither is the technology that protects it. Think of it like this: you can’t use a single key to open every door, and you can’t use a single DRM system for every device and platform. When we talk about DRM-protected content, it’s almost always being secured by one of three major players.
To get your content to your audience, you need to understand the “big three” that run the show: Google Widevine, Apple FairPlay, and Microsoft PlayReady. Each one acts as a gatekeeper for a specific ecosystem. Picking the right combination is the only way to make sure you can reach everyone, everywhere. The whole process boils down to encrypting your video, managing secure licenses for viewers, and ensuring only authorized playback happens.
This diagram shows you that basic flow in action.
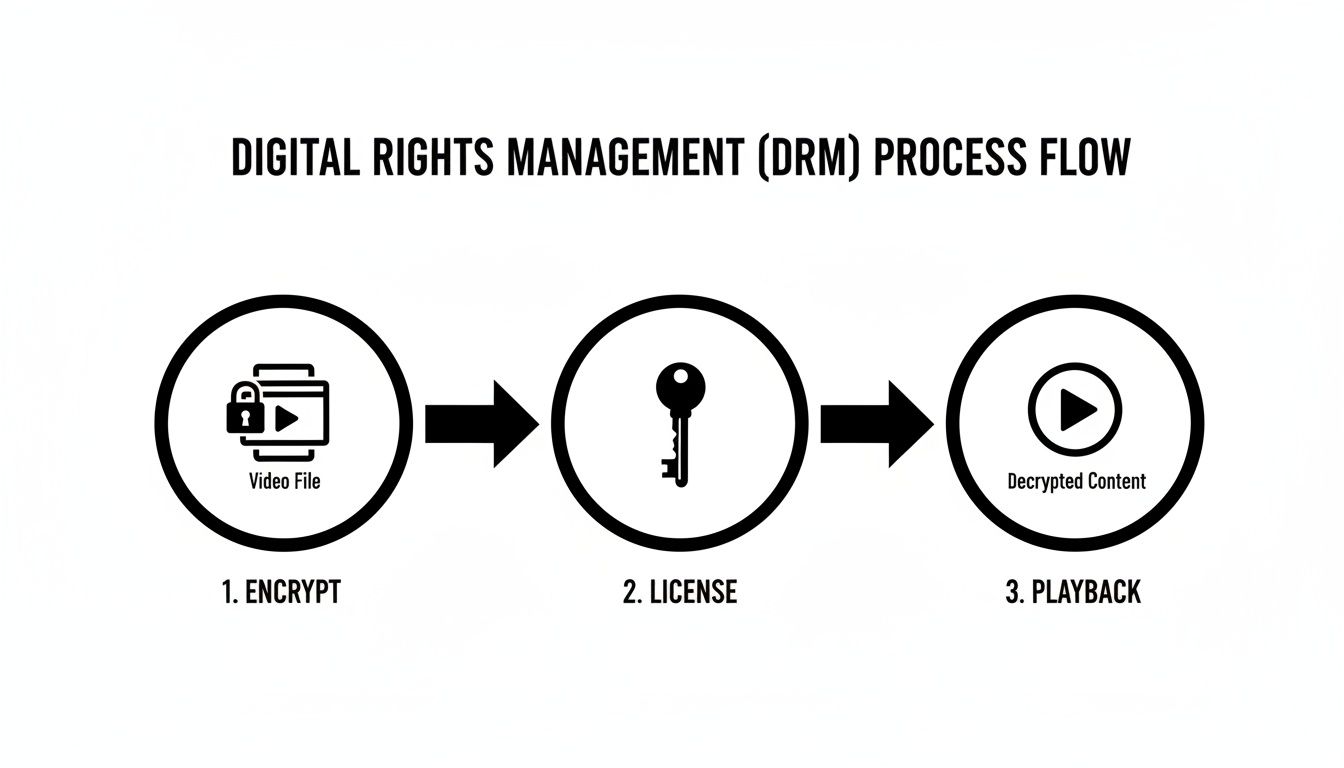
This three-step journey—from locking down the content to delivering a key for playback—is the bedrock of every major DRM system out there.
Google Widevine: The Standard For Android And Chrome
Google Widevine is without a doubt the most common DRM technology on the planet. Why? Because it’s built directly into the world’s most popular browser, Chrome, and the most dominant mobile operating system, Android.
If your audience uses Android phones, Chromecasts, or watches video in a Chrome browser, then Widevine isn’t just an option; it’s a necessity. It’s also flexible, offering different security levels to support everything from low-cost hardware to premium devices with advanced, hardware-level protection.
Apple Fairplay: The Gatekeeper Of The Apple Ecosystem
Want your content to play on an iPhone, iPad, Apple TV, or inside the Safari browser? You’ll need to go through Apple FairPlay. It is the one and only DRM technology for the entire Apple ecosystem, period.
FairPlay is woven tightly into Apple’s hardware and software, creating a secure and seamless viewing experience for anyone inside that walled garden. This exclusivity means any streaming service that wants to reach Apple’s massive user base has to play by FairPlay’s rules. It’s a non-negotiable step for delivering premium video to one of the most valuable consumer markets in the world.
Microsoft Playready: The Versatile Veteran
Microsoft PlayReady is the seasoned veteran of the group, known for its sheer versatility. While it’s the native DRM for Microsoft Edge and the entire Xbox ecosystem, its influence goes much further. You’ll find PlayReady powering all sorts of smart TVs, set-top boxes, and other living room devices.
Its robust feature set makes it a cornerstone of any good multi-DRM strategy, helping you lock down content on a huge range of devices beyond just phones and computers. If you’re building a streaming service and want to be on smart TVs, PlayReady is essential.
Comparison Of Major DRM Technologies
Because each system is vital for a specific set of platforms, a multi-DRM strategy is the only way to effectively protect and deliver your content to everyone. The table below breaks down the big three at a glance.
| DRM System | Developed By | Primary Platforms | Key Use Case |
|---|---|---|---|
| Widevine | Chrome, Android, Firefox, Chromecast | Protecting content for the vast majority of web and mobile users outside the Apple ecosystem. | |
| FairPlay | Apple | iOS, macOS (Safari), tvOS, iPadOS | The exclusive solution for reaching all users on Apple devices. |
| PlayReady | Microsoft | Microsoft Edge, Xbox, Smart TVs, Set-Top Boxes | Securing content on “living room” devices and complementing a multi-DRM setup. |
As you can see, no single DRM can do the job alone. To create a smooth viewing experience, modern streaming services use a multi-DRM setup. This way, the platform can automatically detect what device a person is using and serve the stream with the correct DRM attached. It ensures everyone can watch, whether they’re on an iPhone, an Android tablet, or their smart TV.
To go deeper, check out our detailed article on implementing DRM for video and see why a unified approach is so important for modern streaming.
Weighing the Benefits and Challenges of DRM
Putting DRM in place is a big decision for anyone creating or sharing content. It comes with some serious perks, but it’s not a magic bullet. To really get it, you need to look at both sides of the coin: the powerful protections that make it a must-have for premium media, and the real-world headaches that can come with it.
Understanding this trade-off is crucial. For creators, it’s all about protecting their work and building a business that can last. For the rest of us, it helps explain the technology that powers the massive streaming libraries we use every day.
The Clear Benefits of Using DRM
At its core, DRM gives content owners the final say over how their digital property is used. This control leads to some very real business advantages that have fundamentally shaped how we watch movies and listen to music today.
The most obvious benefit is piracy prevention. By locking down content with encryption and controlling access with secure licenses, DRM makes it extremely difficult for people to illegally copy and share media. This directly protects the money that would otherwise vanish into the world of illegal downloads and streams.
DRM also unlocks flexible revenue models. Think about it—without DRM, business models like subscriptions (Netflix), rentals (Apple TV), or even free, ad-supported shows (Tubi) would be almost impossible to manage. It’s the technology that makes a rented movie disappear after 48 hours or ensures only paying subscribers can binge-watch the latest hit series.
Finally, it helps companies meet strict licensing requirements. Movie studios don’t just hand over their blockbusters; they often demand top-tier DRM protection as part of the deal. If a streaming service wants to offer high-value films and shows, implementing a solid DRM system isn’t optional—it’s the only way to get legal access.
Addressing the Common Challenges
For all its benefits, DRM isn’t a simple plug-and-play solution. One of the biggest concerns is the risk of user friction. If the DRM is clunky or poorly set up, paying customers can run into playback errors, discover their device isn’t compatible, or get stuck in confusing login loops. Nothing sours a viewing experience faster.
Then there’s the implementation complexity. Juggling the big three DRM systems—Widevine, FairPlay, and PlayReady—isn’t for the faint of heart. It takes specialized technical know-how to build and maintain the secure license servers and infrastructure needed to make it all work smoothly.
The Fair Use Debate: An ongoing conversation pits DRM against the principle of “fair use”—the idea that you can use snippets of copyrighted material for things like commentary or parody. Critics worry that some DRM systems are so restrictive they might stop someone from using content they legally bought in a way that should be considered fair.
Lastly, the cost of implementation is a real factor. Licensing the technologies and setting up the server architecture comes with upfront and ongoing costs. But for most businesses, it’s a necessary investment to protect assets that are far more valuable.
The market numbers tell the story. The global Digital Rights Management market was valued between USD 5.20 to USD 6.16 billion in 2024 and is on track to hit as much as USD 6.72 billion by 2025. This isn’t just a niche technology; it’s a cornerstone of the digital economy. You can dive deeper into these trends in the digital rights management market report. This growth is heavily steered by North America, which makes up about 46.3% of all DRM usage worldwide.
How to Simplify Your Multi-DRM Workflow

Juggling the technical demands of Widevine, FairPlay, and PlayReady can feel like an impossible task. If you’re a developer or a business looking to launch a secure streaming service, the idea of building separate, complicated integrations for each DRM scheme is a recipe for a massive headache. This traditional path is a heavy lift.
In the past, this meant creating and supporting multiple workflows. Each one had its own unique requirements, license server setups, and a long list of things that could go wrong. It was a process that burned through resources and seriously delayed getting your product to market.
Luckily, modern video platforms have completely changed the game. That tangled web of multi-DRM management can now be untangled and streamlined into a single, elegant solution.
The Old Way: A Fragmented Approach
To really get why this is such a big deal, let’s look at how DRM used to be implemented. It was a manual, disconnected process that put a huge burden on development teams.
Picture this: you want to deliver DRM-protected video to people all over the world. To make that happen, your team would have to build:
- A dedicated Widevine integration to handle all the license requests coming from Chrome and Android devices.
- A separate FairPlay setup to manage the very specific certificate and key exchanges required by Apple’s ecosystem.
- And another system for PlayReady to serve licenses to smart TVs, game consoles, and Microsoft browsers.
Each of these systems needs its own server infrastructure, constant upkeep, and a deep well of technical know-how. A single bug in one could shut down playback for a huge chunk of your audience, kicking off a frantic scramble to find and fix the problem. It’s an expensive, complex, and fragile way to do business.
The New Way: A Unified API
Now, let’s compare that mess to a modern, unified approach. Instead of building three separate pipelines, platforms like LiveAPI bring the entire multi-DRM process together into a single, simple API call.
What this means is that your development team only has to interact with one endpoint. Behind the scenes, the platform does all the heavy lifting—it automatically figures out what device the viewer is using and applies the right DRM technology without you having to do a thing.
A unified DRM API abstracts away the complexity. Your application makes one request, and the platform intelligently handles the specific protocols for Widevine, FairPlay, and PlayReady, ensuring seamless and secure playback for every user on every device.
This is a fundamental shift that turns a difficult engineering challenge into a straightforward task. It’s like the difference between building an engine from scratch and just turning the key.
Key Advantages of a Modern Workflow
Switching to a unified DRM solution gives you immediate and powerful benefits, freeing you up to focus on creating great content and a fantastic user experience instead of wrestling with backend infrastructure.
1. Radically Reduced Development Time What used to take months of specialized development can now be done in a tiny fraction of the time. Integrating a single API is exponentially faster than building and testing three different DRM systems from the ground up.
2. Elimination of Maintenance Headaches You can stop worrying about maintaining multiple license servers, keeping security protocols up to date, or patching vulnerabilities for each DRM technology. The platform takes care of all of that for you, giving you enterprise-grade security right out of the box.
3. Guaranteed Cross-Platform Compatibility A unified API ensures your content is protected and plays perfectly everywhere. From iPhones to Android tablets and smart TVs, the system automatically delivers the correct DRM-protected stream for a consistent and reliable user experience. This also works hand-in-hand with other crucial video processes, and you can learn more about how video transcoding prepares files for different devices in our dedicated guide.
At the end of the day, simplifying your multi-DRM workflow lets you launch a professional, secure streaming service with total confidence that your valuable content is safe—all without getting bogged down in the technical weeds.
The Future of Content Protection Technology
The technologies that protect digital content are always playing a high-stakes game of cat and mouse with pirates. As streaming formats and viewer habits change, so do the methods for securing that media. The future of content protection isn’t just about building stronger locks; it’s about creating smarter, more adaptive security systems that can see threats coming and stop them in their tracks.
This constant push for better security is fueled by the explosive growth of the digital economy. More content consumption inevitably means more threats, which in turn drives demand for better protection. It’s no surprise that the Digital Rights Management market is projected to swell to between USD 14.48 billion and USD 28.2 billion by 2034. For a deeper dive into these numbers, you can explore the full report on Market.us.
AI and Proactive Piracy Detection
One of the biggest game-changers on the horizon is the use of artificial intelligence and machine learning. Instead of just reacting after pirated content shows up on sketchy websites, AI-powered systems can now proactively hunt for security holes and suspicious activity as it happens.
Think of it like a digital immune system. These systems sift through enormous amounts of data to spot patterns linked to piracy—things like a sudden, weird spike in license requests from a single IP address or someone trying to access content with a known compromised device. This allows platforms to automatically shut down threats before any real damage is done, shifting the entire security model from reactive to proactive.
The Role of Watermarking and Blockchain
While DRM is fantastic for controlling initial access, other technologies are stepping up to complement it, especially for tracking down leaks after they happen. Forensic watermarking, in particular, is becoming a powerful partner to traditional DRM.
Here’s how it works: the technology embeds an invisible, unique ID into every single video stream sent to a user. If that specific stream ever pops up on a pirate site, the watermark can be pulled out to trace the leak directly back to the source account. This alone is a huge deterrent against casual screen recording and password sharing.
Beyond that, people are exploring technologies like blockchain to create a transparent, unchangeable ledger of content ownership and licensing. This could drastically simplify rights management and help make sure creators are paid what they’re owed.
Looking Ahead: The real magic is in how these technologies are coming together. The next generation of security will be a multi-layered defense, combining DRM for access control, forensic watermarking for traceability, and AI for real-time threat analysis.
New Frontiers in VR and AR
As we move into new kinds of media like virtual reality (VR) and augmented reality (AR), we’re facing a whole new set of security puzzles. Protecting an immersive, interactive experience is a far more complex challenge than just locking down a video file.
The future of content protection has to be built for these new, complex worlds, making sure that interactive digital assets are just as secure as the movies and shows we watch today. That’s why picking a security partner who is already thinking about and preparing for these future challenges is more critical than ever.
Frequently Asked Questions About DRM
Even after you get the hang of how DRM-protected content works, a few practical questions always seem to pop up. Let’s tackle some of the most common ones to clear up how a real-world content security strategy actually plays out.
Can DRM Be Bypassed?
In a word, yes. No security system is 100% impenetrable, and determined pirates are always hunting for the next vulnerability in any DRM technology. But thinking about it that way misses the point entirely.
The goal of a strong, modern DRM isn’t to be theoretically perfect forever. It’s to make piracy so incredibly difficult, time-consuming, and expensive that it’s just not worth the effort for the average person.
Multi-DRM systems from providers like Google, Apple, and Microsoft are massively complex and are constantly being updated to close security gaps. By sticking with these official, up-to-date systems, you create a powerful deterrent that stops widespread, casual piracy dead in its tracks. It raises the bar for entry so high that most would-be pirates simply give up.
Does DRM Affect Video Quality?
This is a big misconception. Many people assume that wrapping content in DRM automatically hurts video quality or introduces buffering. The truth is, the DRM technology itself—the encryption and the license exchange—has zero impact on the quality of the video or audio files. The pixels are the same before and after.
Where you can run into trouble is with a sloppy implementation. If your license server takes too long to respond or the video player isn’t properly configured for the DRM handshake, the viewer might notice a slight delay before the video starts.
Key Takeaway: DRM technology itself doesn’t touch the quality of your video stream. Performance hiccups like startup delays are almost always a result of a clunky integration or slow server response times—not the DRM itself. In a well-built system, the security process is completely invisible to the viewer.
Is DRM Necessary For All Video Content?
Definitely not. The decision to use DRM really comes down to your content and your business model. If you’re putting out marketing videos, public tutorials, or hosting user-generated content, you actually want it to be as open and shareable as possible.
DRM becomes critical when the content is the product. If your business is built on any of the following, strong protection is non-negotiable:
- Subscription Services: Keeping your premium shows and movies exclusive to paying members.
- Transactional Content: Securing rentals or one-time purchases of films.
- Live Events: Controlling access for pay-per-view sports, concerts, and other live broadcasts.
- Confidential Media: Protecting sensitive corporate training videos or internal communications.
At the end of the day, ask yourself this: would unauthorized access to your video lead to a direct loss of revenue or a breach of your licensing deals? If the answer is yes, then implementing DRM is one of the most important business decisions you can make.
Ready to protect your content without the headache? LiveAPI offers a unified multi-DRM solution that simplifies security, letting you focus on creating amazing video experiences. Secure your streams and launch faster by visiting https://liveapi.com.