DRM for video is really just a way to lock up your content so only the right people can watch it. It’s a set of technologies that encrypts your videos, making sure that only viewers with a special digital key—like your paying subscribers—can unlock and play them. This protects your revenue, your content, and your business.
What Is DRM for Video and Why Is It Essential?
Think of your premium video library as a high-security bank vault. You wouldn’t just leave the door unlocked for anyone to wander in and help themselves. Digital Rights Management (or DRM) is the advanced security system for that digital vault.
It’s far more than a simple password. DRM is a complex system that combines powerful encryption, a secure key-swapping process, and specific playback rules to protect your video from the moment it’s uploaded until it hits a viewer’s screen.
In a world where a pirated video can be shared globally in minutes, protecting your content isn’t just a good idea—it’s a core business necessity. Piracy isn’t just about a few lost sales; it can devalue your entire brand and undercut the business model you’ve worked so hard to build.
The Business Case for DRM Protection
Putting DRM in place is less of a technical task and more of a strategic business decision. It’s all about directly protecting your most valuable assets. Here’s a closer look at what it does for you:
- Secures Your Revenue: Whether you run a subscription service (SVOD), a pay-per-view platform (TVOD), or an ad-supported model (AVOD), DRM makes sure that only legitimate viewers are watching. It closes the backdoors that let pirates siphon away your income.
- Protects Your Intellectual Property: Your content is your product. DRM is what enforces your copyrights, stopping the illegal copying and sharing that chip away at the value of your creative work.
- Unlocks Premium Content Deals: If you want to license blockbuster movies or popular TV shows, you’ll find that major studios have a non-negotiable requirement: you must have robust DRM. Without it, you can’t even get in the door to access those high-value catalogs.
- Maintains Brand Integrity: By controlling where and how your videos are seen, you preserve the quality and context of the viewing experience. This is crucial for how people perceive your brand.
The global demand for this kind of protection is massive and growing. The Digital Rights Management (DRM) market was recently valued at around $5.82 billion and is expected to climb to $13.41 billion soon. This growth is fueled by the explosion of digital media and the constant threat of piracy. You can dig into the numbers and trends in the full market report.
Understanding the Three Pillars of Video DRM

When people talk about video DRM, they’re not talking about one single piece of technology. The reality is more like an ecosystem built on three major systems, each deeply woven into its own tech universe. A good analogy is thinking of them like different national power grids—you can’t just plug an American appliance into a European wall socket without the right adapter.
This is exactly why a multi-DRM strategy isn’t just a good idea; it’s the industry standard. To get your content in front of everyone, everywhere—from their Android phone to their Windows laptop to their Apple TV—you have to speak the native security language of each platform.
Google Widevine: The Powerhouse for Android and Chrome
Google’s Widevine is easily the most common DRM solution on the planet. Its massive footprint is thanks to being the default protection for both the world’s most popular mobile operating system, Android, and the most used web browser, Google Chrome. That’s a staggering number of devices.
Widevine is built around a hardware-backed security model with different levels of trust (L1, L2, and L3). The gold standard is L1, where all the sensitive stuff—like decrypting the video—happens inside a secure, isolated part of the device’s main chip called a Trusted Execution Environment (TEE). This makes it incredibly tough for anyone to snatch the video stream, which is why services like Netflix and Disney+ demand L1 security for playing anything in HD or 4K.
Because Widevine is so deeply integrated into Android and Chrome, it’s the automatic choice for protecting content headed to the vast majority of smartphones, tablets, smart TVs, and web browsers.
Microsoft PlayReady: Securing Windows and More
Developed by Microsoft, PlayReady is the go-to DRM for the entire Windows world. That means every device running Windows, the Microsoft Edge browser, and—crucially—gaming consoles like the Xbox. But its reach doesn’t stop at PCs.
PlayReady is widely respected for its incredible flexibility. It’s designed to support all sorts of business models, from permanent purchases and timed rentals to monthly subscriptions. This versatility makes it a favorite for content owners who want to implement creative monetization strategies across a wide array of devices, including many smart TVs and set-top boxes that license the technology.
Apple FairPlay: The Gatekeeper of the Apple Kingdom
Apple’s FairPlay Streaming (FPS) is the one and only DRM for the Apple ecosystem. If you want to deliver protected video to an iPhone, iPad, Mac (using Safari), or Apple TV, you have to go through FairPlay. It’s a closed garden, and Apple holds the key.
FairPlay is hardwired into Apple’s hardware and software, using the Secure Enclave in Apple chips to handle decryption securely. It’s also a critical part of how Apple’s own streaming protocol, HLS (HTTP Live Streaming), delivers protected video. If you’re interested in the nuts and bolts, you can learn more about what HLS streaming is and its role in modern video delivery. This tight control gives users a seamless, secure experience but means you must implement FairPlay to reach Apple’s massive audience.
Comparing the Major Video DRM Systems
To get a clearer picture, let’s break down how these three systems stack up against each other. Each has its own turf and its own strengths, which is why a comprehensive streaming service needs to support them all.
| DRM System | Developer | Supported Platforms | Key Feature |
|---|---|---|---|
| Widevine | Android, Chrome, Firefox, Edge, Chromecast, Android TV | Hardware-backed security levels (L1/L3) for varying protection needs. | |
| PlayReady | Microsoft | Windows, Edge, Xbox, Smart TVs, Set-Top Boxes | Highly flexible licensing rules that support rentals, subscriptions, and purchases. |
| FairPlay | Apple | iOS, iPadOS, macOS (Safari), tvOS (Apple TV) | Exclusive and deeply integrated into Apple’s hardware and software ecosystem via HLS. |
The takeaway is simple: you can’t pick just one. A typical viewer might start a movie on their Windows PC (PlayReady), switch to their Android phone on the train (Widevine), and finish it on their Apple TV at home (FairPlay). To make that journey seamless and secure, your video workflow has to handle all three, making a multi-DRM setup an absolute must for any modern streaming platform.
How the Video DRM Workflow Actually Works
Think of the video DRM workflow like sending a high-value package. You wouldn’t just drop it in the mail; you’d put it in a locked box, send the key separately via a secure courier, and ensure only the intended recipient can open it. That’s exactly what happens with your video, just in a matter of milliseconds.
The entire process is a carefully choreographed dance between your video content, a license server, and the viewer’s device. It’s designed to be completely invisible to your audience but absolutely essential for you as the content owner. Let’s break down how it all comes together.
Step 1: Content Encryption and Packaging
The journey starts the second you upload a video. Before it ever hits a server for storage or streaming, the raw video file is scrambled using a powerful encryption algorithm—the industry standard is AES-128. This is like locking your video content inside a digital vault.
At the same time, a unique Content Encryption Key (CEK) is created. This is the one and only key that can unlock that specific vault.
Next, the encrypted video needs to be prepared for streaming. It gets packaged into adaptive bitrate formats like MPEG-DASH or HLS. But this isn’t just about making it stream smoothly. During this step, a critical piece of metadata called the Protection System Specific Header (PSSH) is embedded into the video’s manifest file. The PSSH is essentially a signpost that tells the video player which DRM system to use (Widevine, PlayReady, or FairPlay) and where to go to get the key. This often happens alongside the processes we cover in our guide on what is video transcoding.
Step 2: The Secure License Request
When a viewer hits “play,” their video player (whether in a browser or an app) reads the manifest file and immediately sees the PSSH data. This kicks off the security handshake.
The player does two things almost instantly:
- It sends a license request to the DRM license server whose address is listed in the manifest.
- This request contains the PSSH info, along with details about the viewer’s device and their authentication status.
The license server acts as the central gatekeeper. It checks the viewer’s credentials against your business rules. Are they a paying subscriber? Are they watching from an approved country? Is their device permitted?
Once the server validates the viewer, it generates a license containing the Content Encryption Key (CEK). Crucially, this license is itself encrypted using a key unique to the player, making sure only that specific device can even read it.
This three-step journey from encryption to playback is illustrated below.
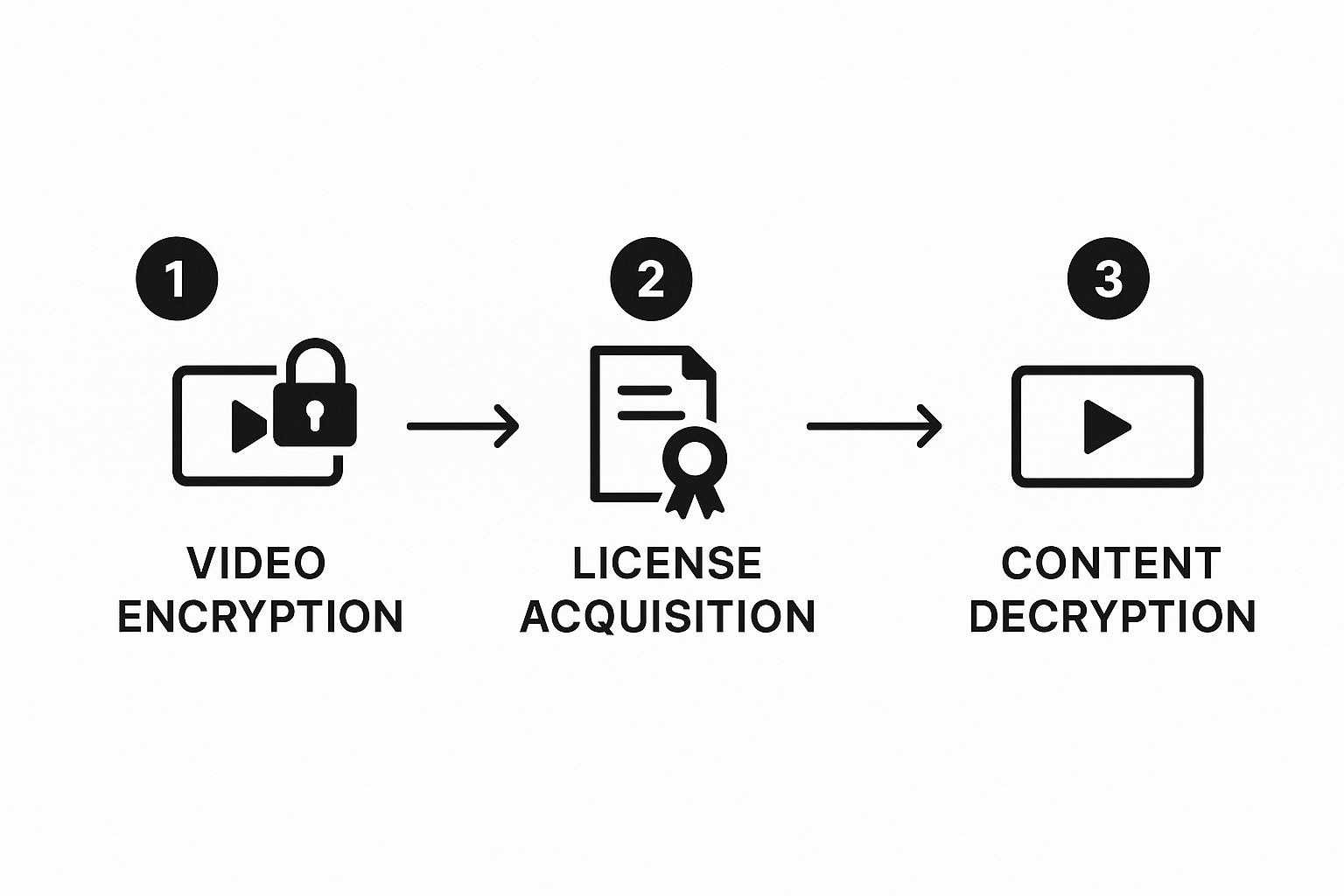
As you can see, the video, license, and player work in concert to create a viewing experience that feels seamless to the user but is incredibly secure behind the scenes.
Step 3: Decryption and Secure Playback
With the license now in its possession, the video player hands it off to a highly secure part of the device known as the Content Decryption Module (CDM). The CDM is a hardware-level “black box” that’s specific to each DRM system—for example, Google Chrome has a Widevine CDM, while Apple devices have a FairPlay CDM.
Inside this protected environment, the CDM decrypts the license to access the original Content Encryption Key. It then uses that key to unscramble the video stream in real-time, piece by piece, just moments before the frames are sent to the screen.
This final step is what makes the whole system so robust. The decrypted video frames are never exposed to the device’s main operating system or other software. They are passed directly from the secure CDM to the display, which is why trying to screen-record DRM-protected content almost always results in a black screen. This level of security is why the media and entertainment DRM market alone, valued at USD 5.49 billion, is projected to soar to USD 16.49 billion as content protection becomes non-negotiable. You can see the full market analysis over at Straits Research.
Choosing Your Video DRM Implementation Strategy

Alright, you’ve got the basics of how video DRM works under your belt. Now comes the big question: how do you actually get it working for your content? This isn’t just about picking a technology; it’s a major strategic decision that will shape your budget, your product timeline, and how you manage security for the long haul.
You’re essentially standing at a crossroads with a classic “build vs. buy” choice, plus a third “hybrid” path that sits somewhere in the middle. Each route has its own set of trade-offs when it comes to cost, complexity, and control. The right answer really depends on your team’s skills, how much you’re willing to spend, and what your ultimate business goals are.
The In-House DRM Build
The first path is to build your own DRM system from scratch. This is the ultimate power move—it gives you absolute control over every single piece of your content security. You own it all, from the way the license server thinks to how it plugs into your existing subscriber database. For massive operations, this can even lead to lower per-license costs over time.
But let’s be clear: this path is not for the faint of heart. The upfront cost is massive. You’re not just buying servers; you’re hiring a dedicated team of highly specialized security and video engineers. On top of that, you have to navigate complex and expensive licensing deals directly with Google, Microsoft, and Apple. It’s a huge undertaking.
- Pros: Total customization and control. At a gigantic scale, it could become more cost-effective.
- Cons: Extremely high initial investment, requires a very specific and expensive engineering skillset, long time-to-market, and a never-ending maintenance responsibility.
The DRM-as-a-Service (DaaS) Partner
This is, by far, the most common route taken today. Partnering with a managed DRM-as-a-Service (DaaS) provider is like hiring a special forces team to handle your video security. These companies live and breathe DRM. They’ve already built the sophisticated infrastructure, secured the licenses, and they take care of all the updates and maintenance headaches.
This approach flips the script on cost and speed. Instead of spending months or even years building, you can be up and running in days. It frees up your team to do what they do best—create amazing content and improve your platform. The DaaS partner handles the messy, complicated business of license delivery behind the scenes. Our guide on how to stream live video shows just how much a managed service can simplify these kinds of complex workflows.
The DaaS model has really leveled the playing field, giving smaller companies access to the same studio-grade protection that was once only available to the biggest players. It makes top-tier content security accessible.
This approach is a key reason the market has exploded. Europe, for example, is a major DRM hub, accounting for over 30% of the global market with a value hitting around USD 1.52 billion. Cloud-based DaaS providers have made it simple for businesses of all sizes to adopt robust security.
The Hybrid DRM Approach
The third option is a middle ground. A hybrid strategy lets you mix and match, combining your own in-house components with a DaaS provider’s services. For example, you might build the business logic that checks if a user is a paying subscriber, but then hand off the core task of actually creating and delivering the DRM license to a specialized partner.
This gives you a great balance of control and convenience. You get to keep sensitive user data and business rules firmly within your own walls while offloading the most technically demanding and resource-heavy parts of the DRM puzzle.
- Best for: Companies with unique security or integration requirements that don’t want to take on the full burden of running a complete DRM system.
- Considerations: It still demands more in-house technical know-how than going pure DaaS, and you have to be careful about how your internal systems talk to the provider’s API.
Ultimately, picking your strategy is a balancing act. You need to take a hard look at your team, your budget, and how quickly you need to get to market. The right choice is the one that best protects your content while pushing your business forward.
Integrating DRM into Your LiveAPI Workflow

Knowing the theory behind video DRM is one thing, but actually putting it to work is where it counts. For developers, the goal is to lock down content without getting tangled up in endless configuration files and complicated server setups. This is exactly where a modern, API-driven platform shines.
Using a service like LiveAPI, you can go from a simple idea to a fully protected video stream in just a few straightforward steps. Forget about building and maintaining your own license servers or manually juggling encryption keys. You just tell the API what you need, and it handles the heavy lifting.
This section is a practical walkthrough of how to enable robust, multi-DRM protection right inside your LiveAPI environment. We’ll look at the specific API calls and see just how easy it is to secure your valuable video assets. This isn’t abstract theory; it’s a hands-on guide for getting your streams protected.
Activating DRM Protection in Your Stream
The first move is always to enable DRM when you create the stream itself. You do this by simply adding a drm object to your API request. Think of it as flipping the main security switch for your content.
Just by including this object, you’re telling LiveAPI to encrypt the video and get it ready for secure playback. If you skip this, the video will be streamed without any protection, so this is the foundational command for your entire DRM setup.
Let’s look at a basic example. When creating a new stream via the API, your request body would include this simple structure:
{ “name”: “My Secure Event Stream”, “drm”: {} }
That’s it. Just adding the empty drm object tells the system to apply its default, high-security encryption. From here, you can start layering in more specific configurations to tailor the protection to your exact needs.
Configuring Your Specific DRM Providers
Flipping the switch is a great start, but a real multi-DRM strategy means specifying which systems you want to support. LiveAPI makes it simple to configure Widevine, PlayReady, and FairPlay, ensuring your content can reach virtually any device securely.
You do this by adding provider-specific settings inside that drm object. This gives you fine-grained control over how each system behaves.
- Widevine & PlayReady: For these two, the key piece of information is the
license_url. This is the endpoint your video player will ping to grab the decryption key. - FairPlay: Apple’s system is a bit more involved. It needs a
certificate_urlto fetch the FairPlay certificate and alicense_urlfor the key. It also requires anask(Application Secret Key) for an extra layer of verification.
Here’s a more complete JSON snippet showing how you’d set up all three major DRM providers for your video:
{ “name”: “My Multi-DRM Protected Stream”, “drm”: { “widevine”: { “license_url”: “YOUR_WIDEVINE_LICENSE_URL” }, “playready”: { “license_url”: “YOUR_PLAYREADY_LICENSE_URL” }, “fairplay”: { “license_url”: “YOUR_FAIRPLAY_LICENSE_URL”, “certificate_url”: “YOUR_FAIRPLAY_CERTIFICATE_URL”, “ask”: “YOUR_APPLICATION_SECRET_KEY” } } }
This setup guarantees that whether a viewer is on Chrome, Edge, or Safari, the player knows exactly where to go to securely get the license it needs to play your video.
Practical Implementation and Best Practices
Once your configuration is set, you’ve got a solid security layer in place. But a successful integration is about more than just API calls; it’s about making sure the experience is seamless for your legitimate users while keeping pirates out.
A critical best practice is to handle your license URLs and secret keys with care. Never hardcode sensitive information like your FairPlay ask directly into your client-side apps. These credentials belong on your backend, stored securely as environment variables or managed through a secrets management service.
The beauty of an API-first approach is its automation capability. You can programmatically create, update, and manage DRM settings for thousands of video assets without manual intervention, making it a highly scalable solution for content protection.
To make sure everything is running smoothly, follow these key steps:
- Use a Test Environment: Always test your DRM configuration in a staging environment before pushing it to production. This helps you catch any issues with your license server or player setup early.
- Validate Player Compatibility: Double-check that your video player (whether it’s Shaka Player, video.js, or a native mobile player) is correctly configured for the EME workflow and can communicate with your specified license URLs.
- Monitor for Errors: Keep a close eye on your player-side error logs. Problems like failed license requests are often the first sign of a misconfiguration in your DRM settings or an issue with your license provider’s endpoint.
By baking DRM for video protection directly into your API workflow, you turn a complex security challenge into a manageable, automated process. This lets you focus on what you do best—creating great content—knowing it’s protected by studio-grade security on every platform.
Common Questions About Video DRM Answered
As we’ve seen, DRM for video is a crucial part of any serious content protection strategy. But because it’s a complex technology working behind the scenes, it naturally brings up a lot of questions.
Let’s tackle some of the most common ones we hear. Think of this as a practical FAQ to clear up any confusion and help you understand how DRM really works in the real world.
What Is the Difference Between DRM and Encryption?
This is probably the most frequent question, and it’s a great one. People often use the terms interchangeably, but they aren’t the same thing. It’s better to think of encryption as one vital piece of the much larger DRM puzzle.
Imagine you have a valuable document. Placing it in a high-tech safe and locking it is the encryption. It scrambles the content, making it unreadable. But that’s only half the battle. You still need a system to decide who gets a key, how they get it, and what they’re allowed to do once they open the safe.
That entire security system—the armored truck that delivers the keys, the guard who checks IDs, and the rules about who can open the safe—that’s the DRM. It includes the encryption but also manages the secure delivery of decryption keys and enforces your business rules (like “no screen recording”).
So, in a nutshell: encryption is the lock, and DRM is the complete security service built around that lock.
Does DRM Negatively Impact the User Experience?
This is a totally fair question, especially if you remember the early days of DRM. Back then, it could be clunky, requiring weird plugins and sometimes failing for legitimate, paying customers. It was a headache.
Thankfully, those days are long gone. Modern DRM systems like Widevine, PlayReady, and FairPlay are engineered to be completely invisible to your audience. The whole security handshake, from the player requesting a license to the content being decrypted, happens in the background in a fraction of a second.
A user with a proper implementation should have no idea DRM is even there. They hit play, and the video starts. The only time they might notice it is when it’s doing its job—for instance, by preventing screen capture software from recording the video, which just shows a black screen.
- Seamless Playback: The process is so fast it doesn’t add any buffering or lag.
- No Plugins Needed: It’s all built right into modern browsers and operating systems. No more asking users to install Flash or Silverlight.
- Quality is Unaffected: DRM doesn’t compress or alter the video or audio quality in any way.
The goal of modern DRM is to be incredibly tough on pirates while being completely frictionless for your customers.
How Much Does Implementing a DRM Solution Cost?
There’s no single price tag for DRM—the cost depends entirely on the path you take. Your options generally fall into two very different buckets: building it yourself or using a managed service.
Building In-House: This is the Mount Everest of video engineering and, by far, the most expensive approach. You’d be looking at:
- Massive licensing fees paid directly to Google, Microsoft, and Apple.
- The high cost of hiring a dedicated team of specialized security and video engineers (who are hard to find).
- Major, ongoing investment in building and maintaining a global, resilient server infrastructure.
Honestly, this path really only makes sense for a handful of global streaming giants. For almost everyone else, the costs are simply out of reach.
Using a DRM-as-a-Service (DaaS) Provider: This is how most of the industry does it. Instead of building the complex infrastructure, you partner with a service that has already done all the heavy lifting. The pricing model is typically based on usage, like a certain cost per thousand license requests. This approach turns a huge capital expense into a predictable, manageable operating cost, giving you access to the same studio-grade security as the big players.
Is It Possible to Bypass DRM Protection?
Let’s be realistic: no security system in the world is 100% foolproof forever. Determined attackers with deep pockets and a lot of time are always probing for weaknesses, especially when a blockbuster movie is released.
However, modern DRM makes bypassing the protection incredibly difficult, time-consuming, and expensive. It’s not something a casual pirate can do with a simple software tool. With security features running at the hardware level (inside a device’s secure chipset), breaking the encryption requires a sophisticated attack.
The real takeaway is that DRM is an extremely effective deterrent. It completely stops casual piracy and raises the bar for sophisticated theft so high that it’s simply not worth the effort for the vast majority of attackers. By doing so, it protects your revenue and your content from nearly every threat you’ll ever face.
Ready to secure your video content without the complexity? LiveAPI integrates robust, multi-DRM protection directly into your workflow with simple API calls. Protect your streams and grow your business with our developer-first platform. Learn more about LiveAPI and start building today.





![Best Live Streaming APIs: The Developer’s Guide to Choosing the Right Video Streaming Infrastructure [2026]](https://liveapi.com/blog/wp-content/uploads/2026/01/Video-API.jpg)